NSA: White House Linked Directly To NSA Firm Managing NSLs
The White House is linked to the same firm which provides single point management for electronic surveillance, and supports the process to issue subpoenas used to monitor domestic two-way voice traffic.
It appears this company is intimately aware of the FISA, and the NSLs, having former FBI wiretap experts assigned.
OverviewThe White House and Congress dubiously assert 'state secret claim" on matters already in public record. A quick review of the NeuStar information shows the White House and Congress are asserting the NSA-related information is a "State secret." This claim is dubious, and can be defeated in court as has been done with the AT&T.
NeuStar has openly admitted in official filings, signed under affidavit, related to matters the White House, NSA, and DoJ would like to have suppressed. This is not a bonafide claim of privilege, but we can adversely judge this is more likely related to an effort to stifle lawful public discussion on matters of public interest.
NeuStar has been well linked with the White House. [ #29 ]
Details
The detailed information related to this activity is openly available. It is located in the Securities and Exchange Commission database, and part of the public record.
This is the name of the firm which NeuStar acquired, permitting this easy access to law enforcement records: [Acquisition]
This firm is called a
"single point of contact in managing all day-to-day customer obligations involving subpoenas, court orders and law enforcement agency requests under electronic surveillance laws, including CALEA, the USA Patriot Act of 2001 and the Homeland Security Act of 2002." Ref: page 34
More in re new information: [ Click ]
Note:
"Electronic surveillance laws" indicates the firm is representing itself as knowledgeable of FISA.
Questions:
Former FBI wiretap personnel are assigned the firm/subsidiary Click; note the abbreviations related to these organizations are similar to these at Note 1; and the broader conference attendees at Note 3 ]
We judge based on the plethora of open source material, public admission in documents, and all SEC related material that any discussion about the billing practices by the NSA and its contractors are dubiously called, "State Secret."
Rather, the SEC and open records makes it abundantly clear that the firm has no intention of hiding its activities; or in actually engaging in any bonafide "Secret" activities. Moreover, any claim of "state secret" is more likely related to a desire to suppress public discussion of information already in the public domain, and lawfully filed in open records.
We judge the available open records would well establish the relationships the White House, Gonzalez, and the Senate Cover-up Committee is saying is related to "state secrets." Rather, it remains to be seen how much money is flowing from the telecoms, via lobbying dollars, which are made with the hopes that Congress does not look into the long history of Law enforcement access with the various NSA-related contractors.
We recommend you take seriously the Information here [Information/Notes 1-6], which connects the dots, and provides this subpoean list, and discovery plan.
Discussion
The NeuStar-NSA-subpoena data in the SEC document is confirmation there is a link between NSA, .mil activities, JTTF, and the White House.
This information relates to information.
You will also see multiple common interactions in open sources between DoD installations and this company.
It remains to be understood how the Intel-Link databases fit in with this.
Public documents are available in re discovery
There is an alleged problem with internal controls and accounting, Superior Court DC (Civil Action No. 04-0002814; in re Douglas Armentrout]
Company allegedly prevented Armentrout" from investigating alleged fraudulent accounting practices"Ref
Points:
- Because the firm is publicly engaged in litigation, this dispute has public documents which may be of interest prior to filing FOIA; there is other litigation/party names which may be of interest as we learn more in re NSA.
- This firm is already an SEC-filing company, and has already disclosed that it is related to subpoena process; this cannot be something that is subsequently asserted to be a "national security issue" -- it's already filed with the SEC, public, and part of the public record.
Connection to BellSouth
NeuStar is clearly related to the recent revelations related to the NSA, billings, and BellSouth. This is not in dispute. The company has already filed the following information/sworn affidavits, under penalty of perjury to the SEC:
On November 4, 2005, BellSouth Corporation filed a petition seeking changes in the way our customers are billed for services provided by us under our contracts with North American Portability Management LLC.Click ]
Confirms:
- NSA issue (NeuStar, BellSouth) is squarely within the SEC jurisdiction in re compliance with statutes
- Bell South and NeuStar are related
- There is a link between BellSouth and this contract activity: North American Portability Management
- There was a bonafide communication in Nov 2005
- There is a document memorializing the meetings, agreements, and counsel discussion in re issue
- There was a change from something to something; and management would have had to discuss the reasons for this change
- In light of the NSA revelations in re BellSouth, Management would likely be in a position to discuss the NSA billing issues.
Government Contracts [ Ref ]
1. North American Numbering Plan Administrator, fixed annual fee, level of effort/constant revenue per month
2. National Pooling Administrator, fee per/transaction [More numbers/data = more money, even if the target is not a bonafide link with "big scary thing"?]
1999 -- NeuStar acquired Asset/function, transferred from Lockheed Martin, NSA contractor.
e-mail format:
@neustar.biz [Ex: peter.davis@neustar.biz]
Alternate:
syed dot ali at neustar dot com [syed.ali@neustar.com]
Neustar and Narus are linked in common sites and shared industry contacts.
Judiciary Subpoena/Discovery Alert
Appears DIA may be in some cases putting deliberately false/incorrect names on the subject lines to kept things out of the searches.
Ex: Why is a letter/e-mail related to the DIA classified as a "Science" digital records?
Lobbying
How much money is flowing between the lobbyists and members of Congress on the "net neutrality issue", that could affect desire to give attention to/avoid attention on the AT&T and NSA/internet issues?
Also, by way of history and background, it is useful to explore the Congressional language. NeuStar has been linked with the CLEA as has Narus.
This means the scope of the efforts isn't something that magically appeared over night, but is something that has been progressing over time, is well entrenched, and clearly well understood in the information technology sector.
The issue isn't that the law is or isn’t' applicable -- it is -- but to what extent the White House has used the NSA "compartmentalization" process to ensure the public remained in the dark about the illegal activity.
Open Admission of FISA, Surveillance Subpoena Support
Curiously, NeuStar also reports in the SEC filings that it acquired in 2005 the single firm which managed all "day-to-day customer obligations" involving (apparently) the NSA warrants, and National Security Letters.
What is curious is that this is a single focal point, suggesting that in the absence of court oversight, the White House is well linked with this firm to quickly get access to requests for information related to the Patriot Act, Homeland Security, and NSA surveillance.
Note that the firm does not specifically mention warrants, but more generally states that it is related to "electronic surveillance," suggesting that the White House could simply pick up the phone, self-issue a national security letter, then direct law enforcement to target anyone -- all without any court oversight.
In light of Hersh's confirmation that the NSA is actively monitoring domestic-to-domestic voice communications without a warrant, this appears to be an interesting development to say the least.
Recall Operation Falcon appears to have been contracted through the same Quantico facility, raising the prospect that the NSA data mining and voice interception directly fed into the JTTF-DIA training stateside, in violation of the Posse Comitatus Act.
It appears AT&T, which won the Marine Systems Command contract is the firm which Mr. Hersch is referring.
SigInt: [Maritime Standards ]
Meeting Minutes, attendee list: Click
Note K414 matches DCGS, the ground station information located here Kw = DCGS.
Here is a sample dollar figure you can use to trace through the system from Quantico, through DFAS in Columbus. [If you use this dollar amount, you can trace the specific funding codes back to the paying station, and find the budget analysts at Quantico who are working the AT&T accounts Click ]
Here's what happened
NSA was getting so much information -- untlated to any real threat -- that they started to listen in on calls to screen things out. They bypassed FISA not because they were "too busy", but because NSA was litening to the callers, and the DoJ and NSA Knew the FISA court would reject what they wre doing.
Hersh writes:
the volume and the ambiguity of the data that had already been generated. (“There’s too many calls and not enough judges in the world,” the former senior intelligence official said.) The agency would also have had to reveal how far it had gone, and how many Americans were involved. And there was a risk that the court could shut down the program. Instead, the N.S.A. began, in some cases, to eavesdrop on callers (often using computers to listen for key words) or to investigate them using traditional police methods.In other words, they were using illegally intercepted infrmation -- completely disconnected from a bonafide threat, to then direct law enforcement to engage in pre-textual stops, intelligence gathering, and other targeting.
Now we know:
Entertainment: Bloggers have NSA on the run, you may as well laugh at them
. . . .
The Hague: NSA Rendering Target List
Note: Do not actually do this. You could be arrested.
If you're looking for specific names of people to lawfully render to The Hague, here's a list of someo of the names associated with NSA: [Click ]
For a sample of how quickly the above names can be cross referenced, to pinpoint their exact location, here are some samples:
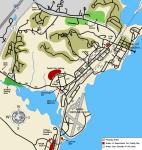 Let's examine:
Let's examine: You'll note in this image, it's fairly easy to land helicopters, and also position various advance teams to the south in the trees. We recommend the The Hague Rendition Team consider a swift movement in the early morning, just as the American war criminals are arriving.
You'll note in this image, it's fairly easy to land helicopters, and also position various advance teams to the south in the trees. We recommend the The Hague Rendition Team consider a swift movement in the early morning, just as the American war criminals are arriving. There should be no problem with overhead wires, and it should be fairly easy to preposition many oil-filled drums as burning-decoys in the nearby water. Jacque Cousteau's journals may have some ideas on some river dinghies. We have never seen any whales in the water, but there are some sure large cows inside the building. These Marine civilians eat too much in Virginia, probably because they have been given too many AT&T donuts as frequent calling-rewards.
Americans are fairly stupid. So bark loudly, they will think that there is another military non-working dog exercise. The Marines like dogs because the dogs can help the stupid Marines find food and prostitutes. Don't show their wives and girlfriends what really goes on with photos. They might really get upset.
The people you are dealing with have already commited war crimes, so there is no need to be afraid of the unknown. We already know what they are capable of doing: Being in the wrong place at the wrong time.
Yes, if you look closely at their commanding general in this photo, you can easily see that he spends too much time jogging, and not enough time lifting weights. Yes, he's a doofus -- be very afraid, he might throw his running shoes at you!



<< Home